- Attackers abused Google Cloud Application Integration to send phishing emails from legitimate Google domains
- Emails mimicked Google notifications, redirecting victims through trusted services
- Nearly 3,200 businesses targeted; most victims in U.S. manufacturing, tech, and finance sectors
Legitimate Google services are, once again, being abused in phishing attacks, successfully tricking targets into clicking malicious links and giving away their login credentials.
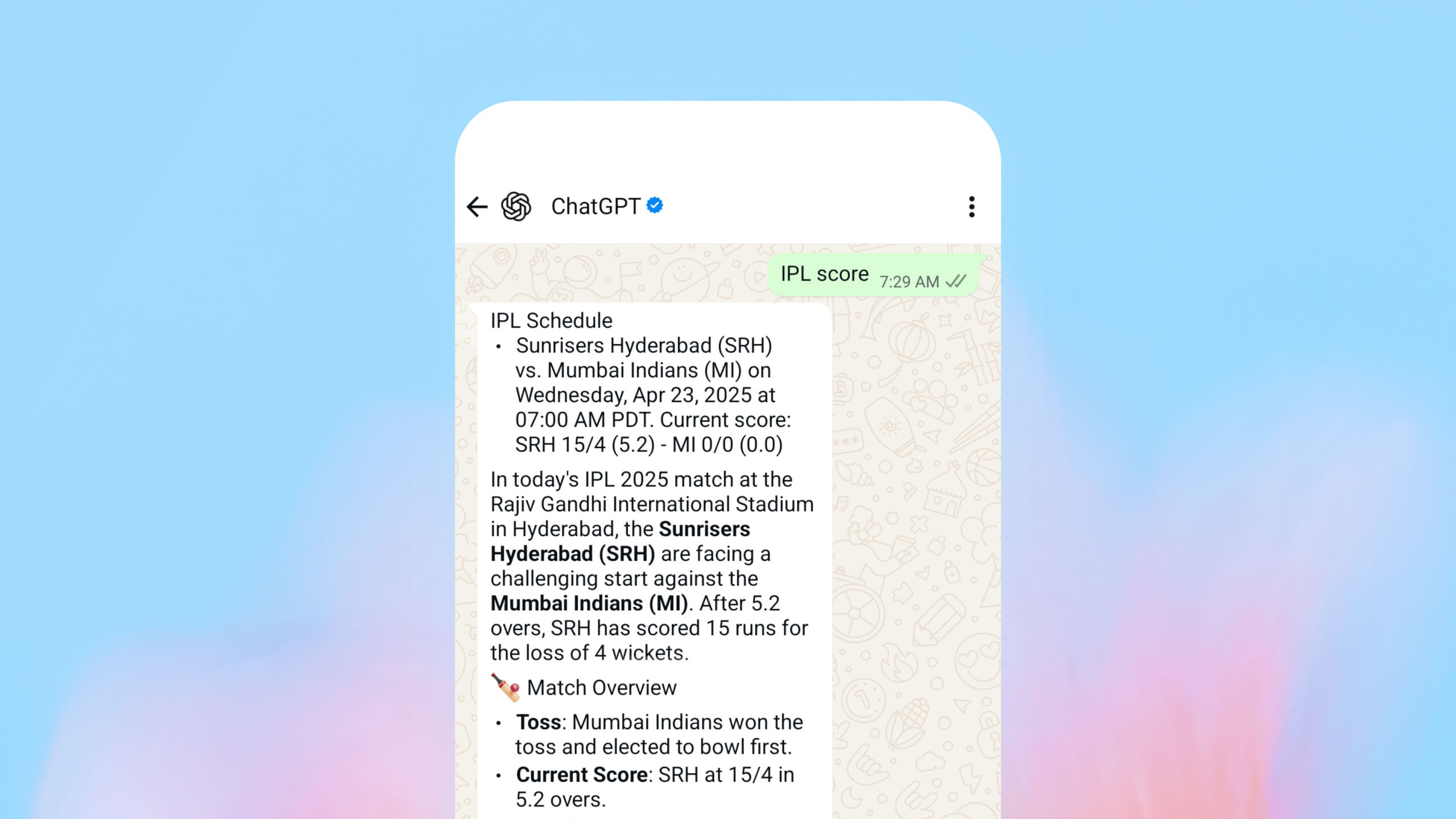
In a newly released report, cybersecurity researchers from Check Point said they’ve seen almost 10,000 emails, being sent to roughly 3,200 businesses in a span of two weeks.
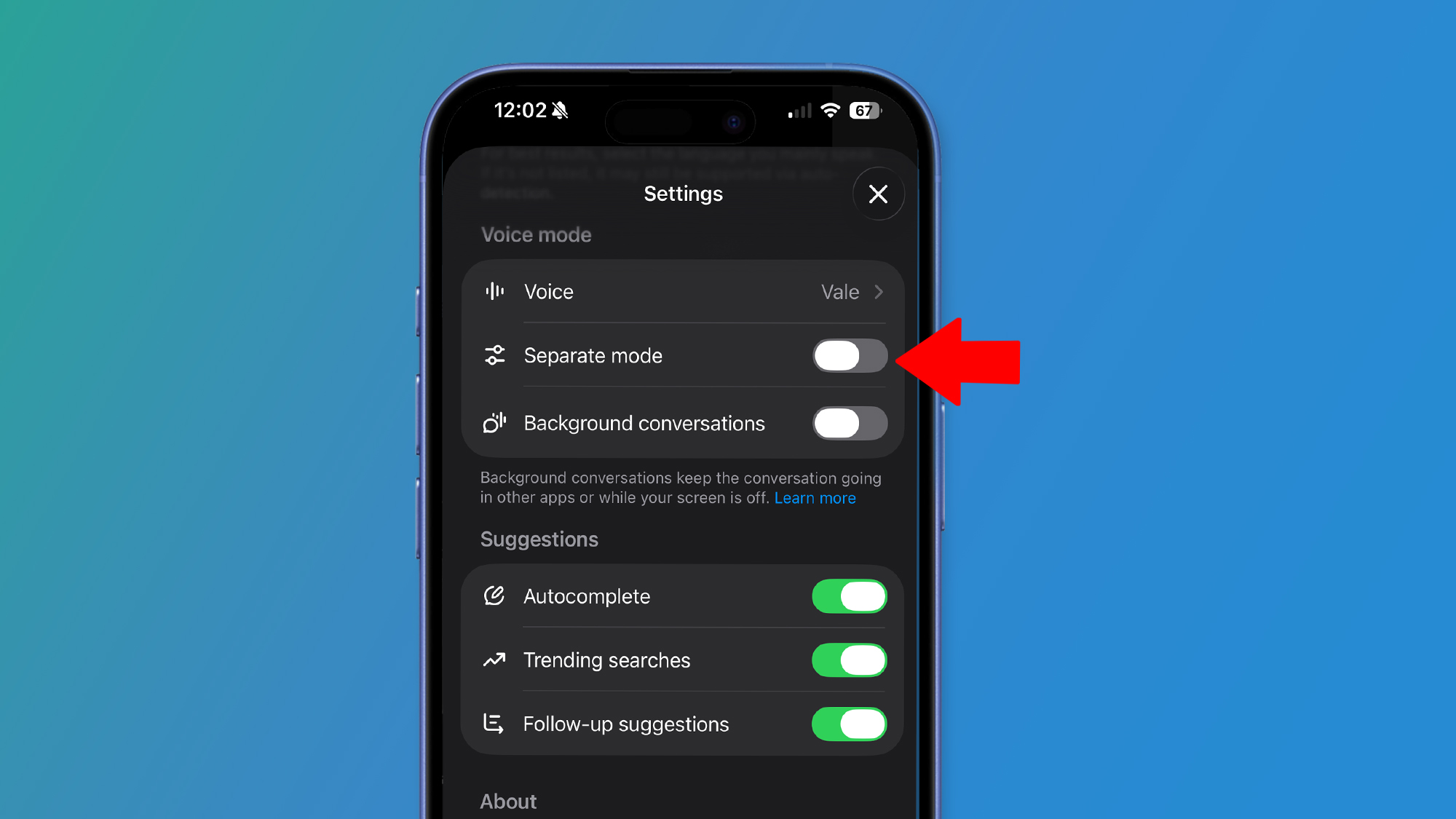
All of the messages were sent from the email account noreply-application-integration@google.com, meaning the attackers were abusing Google Cloud Application Integration.
Targeting manufacturing in the US
This is a managed Google Cloud service that connects applications, APIs, and data sources without needing to write custom code. It lets organizations automate workflows between cloud services, SaaS apps, and internal systems using prebuilt connectors, triggers, and actions. Emails generated through Google Cloud Application Integration often originate from Google-owned infrastructure and domains, meaning they’re sent as part of an automated workflow and can inherit Google’s strong sender reputation.
In phishing campaigns, threat actors can create or compromise a Google Cloud project and configure an integration workflow that sends emails via Gmail APIs or other connected email services. In other words, this is simple abuse – not a breach in Google’s infrastructure.
To make the emails seem even more plausible, the attackers made sure the messages closely followed Google’s notification style, language, and formatting. The most common lures include pending voicemail messages, or notifications about being shared a document.
The link shared in these emails leads to storage.google.cloud.com which is a trusted Google Cloud service. However, it then redirects to googleusercontent.com, where they need to pass a fake CAPTCHA built to block security scanners. Finally, the victims are redirected to a fake Microsoft login page, where they can be tricked into giving away their login credentials.
The majority of the victims were in the United States (48.6%), working in manufacturing/industrial (19.6%), technology/SaaS (18.9%), and finance/banking/insurance (14.8%).
Google told Check Point “several phishing campaigns” abusing Google Cloud Application Integration were already blocked.
“Importantly, this activity stemmed from the abuse of a workflow automation tool, not a compromise of Google’s infrastructure. While we have implemented protections to defend users against this specific attack, we encourage continued caution as malicious actors frequently attempt to spoof trusted brands. We are taking additional steps to prevent further misuse,” Google concluded.

The best antivirus for all budgets
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.